Page Not Found
Page not found. Your pixels are in another canvas.
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Page not found. Your pixels are in another canvas.
About me
Published:
Published:
Published:
Published:
Published:
This is a page not in th emain menu
Published:
Published:
Published:
This page explains how to use IWR6843AOPEVM.
Published:
This paper summarizes resources for Reinforcement Learning.
Published:
This paper summarizes resources for Analog Devices SDR.
Published:
This paper summarizes resources for Nexmon CSI.
Published:
This paper summarizes resources for TI mmwave sensors.
Published:
This paper summarizes resources for Wireless Channel and Radio Propagation.
Published:
This paper summarizes resources for deep learning for beginners.
Published:
This paper summarizes resources for machine learning for beginners.
Published:
This paper summarizes resources for Wireshark.
Published:
This page summarizes resources for Classic Bluetooth and Bluetooth Low Energy. It is still under active update.
Published:
This page summarizes resources for ZigBee and IEEE 802.15.4. It is still under active update.
Published:
This paper summarizes some common and basic usages of Linux. The information is only suitable for beginners.
Published:
This paper summarizes resources for LimeSDR
Published:
This paper summarizes tutorials and resources regarding to digital communications.
Published:
IEEE 802.11 (WiFi) has been used in most of the laptops, smartphones, tablets. The widespread use of WiFi has led to extensive research interests in the area of localization, security, sensing and produced massive successful research outcomes. This paper summarizes some hardware and software resources for WiFi for the research purpose.
Published:
This page summarizes resources for Lego Robot. It is still under active update.
Published:
As a researcher, it is important to write good journal and conference papers. This link summarizes some resources and tips.
Published:
This page summarizes the journals and conferences for communications, computing and security.
Published:
Latex is perfect to prepare report, academic papers and presentations. Different from Word, LaTex may look complicated and difficult to learn in the beginning. It is true, because Latex requires knowledge about the syntax and rules. The learning curve may a little steep but once you become a master, you will love it. You will be able to produce a good looking report without worrying the format any more.
Published:
Our research can be assisted by many useful and easy-to-use tools, for producing fancy figures, creating demonstration video, writing Latex efficiently. There are also many tools to make our everyday work much easier. This page summarizes some useful tools that I am using. Most importantly, most of them are free.
Published:
What is IoT?
Published:
LoRa/LoRaWAN is a new IoT technique which is very suitable for energy efficient and long range communications. This paper summarizes resources for LoRa and LoRaWAN.
Published:
This paper summarizes resources for RTL SDR.
Published:
This page summarizes information for Universal Software Radio Peripheral (USRP).
Published:
This page summarizes information for software defined radio (SDR).
Published:
This page summarizes some publication in the area of machine learning.
Published:
This page provides some resource and my own experience for building a personal website.
Published:
This page summarizes some publication in the area of physical layer security.
Published:
The first Annual General Meeting of the UK-Jiangsu 20+20 World-Class University Consortium was held in Zhenjiang, Jiangsu Province, China, on 9 April 2019.
Key generation is an emerging technique to establish cryptographic keys between legitimate users by extracting randomness from their common channels.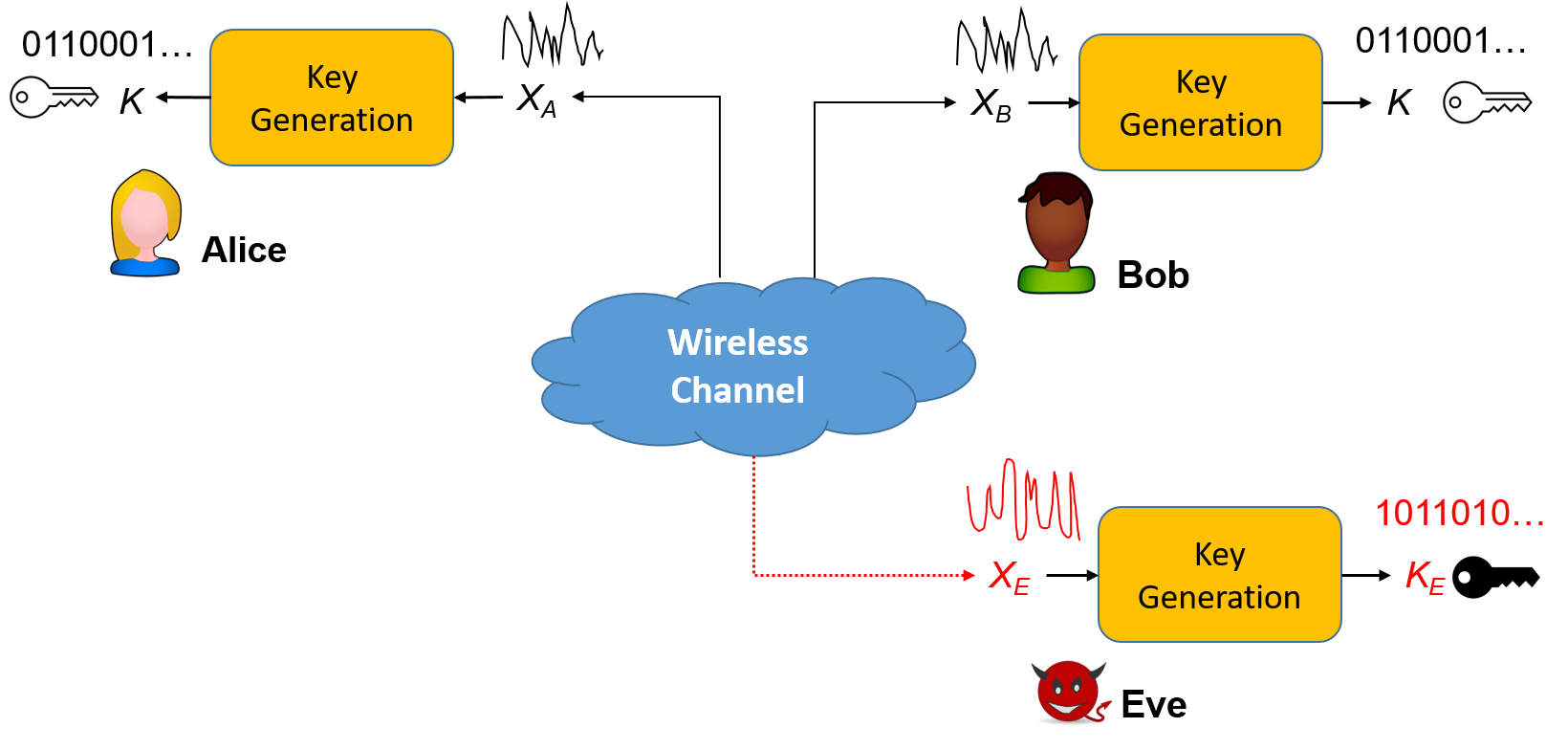
All the components of wireless devices will have slightly different features, e.g., carrier frequency of the oscillators, from the manufacturing processing. Similar to biometric fingerprint, these characteristics are unique and permanent, which can act as the fingerprint of the devices. This technique first requires collecting the device fingerprint and storing them in a database, and then classifies devices by comparing with the stored database whenever a device wishes to join the network.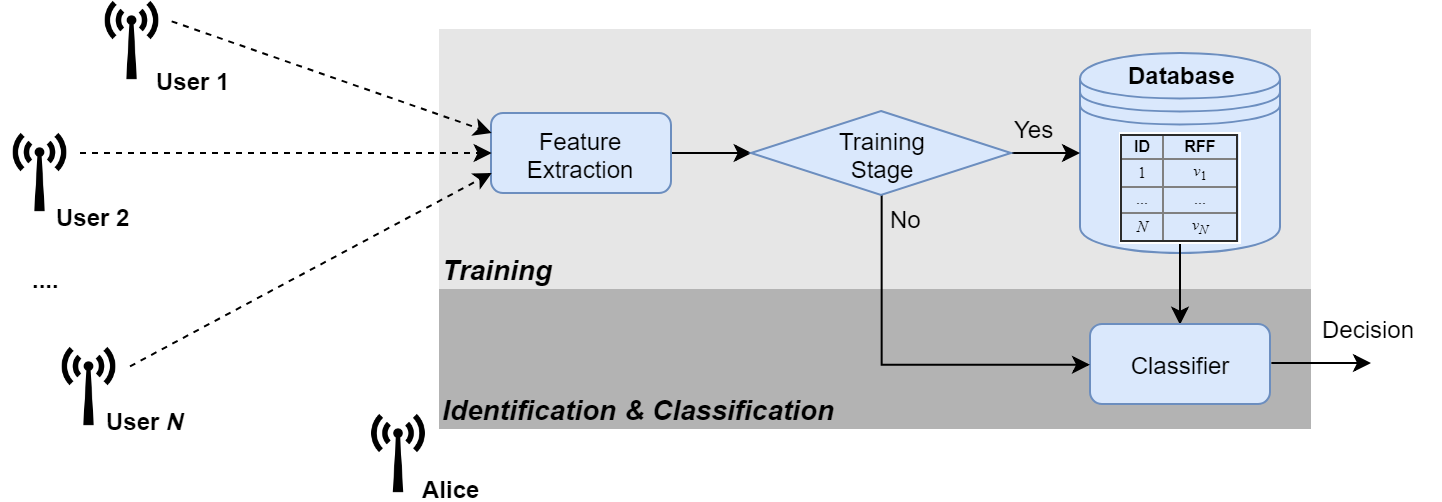
Published:
This is a description of your talk, which is a markdown files that can be all markdown-ified like any other post. Yay markdown!
Published:
This is a description of your conference proceedings talk, note the different field in type. You can put anything in this field.